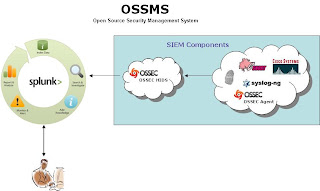
 The purpose of this exercise is to simulate the integration of SIEM (Security Information and Event Management) data into an enterprise indexing repository where we can analyze, generate reports and correlate security relevant events through the use of regular expressions. The ideal goal is to try and build a free OSSMS (Open Source Security Management System). The SIEM devices sit on the border and internal segments of the network and report violations based on the security policy then take corrective action as necessary. Those alerts are forwarded to a filter device; OSSEC HIDS (Host-based Intrusion Detection System) in our scenario that separates our security relevant data from our SIEM devices, in the form of alerts and severity levels based on our organizational security policy, then ingest those events into our indexing engine, Splunk. This way we can filter out any unnecessary alerts/data and pull back only what we want, in a controlled fashion (to help stay within the 500MB of data per day budget and help keep the costs of the Splunk license to $0 to help sustain our free open source security management system). In the end, Splunk should help to enrich the security analysts experience by providing a faster and more efficient way to retrieve, search and query SIEM data from a central location, or across multiple Splunk repositories through its distributed search capability.
The purpose of this exercise is to simulate the integration of SIEM (Security Information and Event Management) data into an enterprise indexing repository where we can analyze, generate reports and correlate security relevant events through the use of regular expressions. The ideal goal is to try and build a free OSSMS (Open Source Security Management System). The SIEM devices sit on the border and internal segments of the network and report violations based on the security policy then take corrective action as necessary. Those alerts are forwarded to a filter device; OSSEC HIDS (Host-based Intrusion Detection System) in our scenario that separates our security relevant data from our SIEM devices, in the form of alerts and severity levels based on our organizational security policy, then ingest those events into our indexing engine, Splunk. This way we can filter out any unnecessary alerts/data and pull back only what we want, in a controlled fashion (to help stay within the 500MB of data per day budget and help keep the costs of the Splunk license to $0 to help sustain our free open source security management system). In the end, Splunk should help to enrich the security analysts experience by providing a faster and more efficient way to retrieve, search and query SIEM data from a central location, or across multiple Splunk repositories through its distributed search capability.Here is my test scenerio, an OSSEC HIDS forwarding alerts to a Splunk server on the same network. Here is what you need to do from a test/configuration stand point:
Setup the OSSEC server
- Install / configure CentOS5
- Download install ossec v1.6 or 2.3
(This is a generic installation, so just accept all of the defaults when running the install.sh script. Read installation files for additional information)
- Inside ossec.conf add a syslog_output block specifying your Splunk system IP address and the port it is listening on: (can be changed to what ever you configuration allows for)

- Now you need to enable the syslog_output module and restart OSSEC:
#/var/ossec/bin/ossec-control enable client-syslog
#/var/ossec/bin/ossec-control restart
-----------------------------------------------------------
Setup SPLUNK
- Install / configure CentOS 5 (I used Ubuntu v9.10 in a VM since I only had one processesor any way)
- Download SPLUNK v4.0.6 tar ball for i386 or 64bit Linux to root's home directory
- Extract the .tar ball in the /opt directory (creates directory /opt/splunk)
# cp $HOME/splunk_linux_name.tar /opt;tar xf /opt/splunk_linux_name.tar
- Make sure you update any local or network firewalls that this communication is traversing and then restart Splunk.
# $SPLUNK_HOME/bin/splunk restart
(Accept the license agreement)
- Open browser and go to http://serverip:8000
* user: admin
*password: changeme
-----------------------------------------------------------
Splunk Configuration
· On the main dash board page, click the Manager link in the top right hand corner of the page
· Under “System Configurations” click on the Data Inputs link
· Click on the UDP link, then click the New button
· Enter the port number (10002 or what ever you entered in during the OSSEC configuration for the port SPLUNK will receive OSSEC alerts from)
· Select “Manual” from the dropdown box pertaining to source type
· Enter in “ossec” in the Source Type text box, then click the Save button
· Now you must enable the data input feed for the port by clicking on the enable link in the row that corresponds to your new UDP port/feed for OSSEC
· Click on the Back to Search link in the top left hand corner of the web browser, generate some alerts from the OSSEC server (or your OSSEC agents) and the alerts should be arriving into SPLUNK soon!!!!
Happy Splunking!!!!!
RESOURCES:
http://www.ossec.net/main/splunk-ossec-integration
http://www.splunk.com/base/Documentation/latest/Installation/InstallonLinux#Tarball_install
#/var/ossec/bin/ossec-control enable client-syslog
#/var/ossec/bin/ossec-control restart
-----------------------------------------------------------
Setup SPLUNK
- Install / configure CentOS 5 (I used Ubuntu v9.10 in a VM since I only had one processesor any way)
- Download SPLUNK v4.0.6 tar ball for i386 or 64bit Linux to root's home directory
- Extract the .tar ball in the /opt directory (creates directory /opt/splunk)
# cp $HOME/splunk_linux_name.tar /opt;tar xf /opt/splunk_linux_name.tar
- Make sure you update any local or network firewalls that this communication is traversing and then restart Splunk.
# $SPLUNK_HOME/bin/splunk restart
(Accept the license agreement)
- Open browser and go to http://serverip
* user: admin
*password: changeme
-----------------------------------------------------------
Splunk Configuration
· On the main dash board page, click the Manager link in the top right hand corner of the page
· Under “System Configurations” click on the Data Inputs link
· Click on the UDP link, then click the New button
· Enter the port number (10002 or what ever you entered in during the OSSEC configuration for the port SPLUNK will receive OSSEC alerts from)
· Select “Manual” from the dropdown box pertaining to source type
· Enter in “ossec” in the Source Type text box, then click the Save button
· Now you must enable the data input feed for the port by clicking on the enable link in the row that corresponds to your new UDP port/feed for OSSEC
· Click on the Back to Search link in the top left hand corner of the web browser, generate some alerts from the OSSEC server (or your OSSEC agents) and the alerts should be arriving into SPLUNK soon
Happy Splunking!!!!!
RESOURCES:
http://www.ossec.net/main/splunk-ossec-integration
http://www.splunk.com/base/Documentation/latest/Installation/InstallonLinux#Tarball_install

No comments:
Post a Comment